The following was taken from Cary Henricks recent talk at Big Data Cyber 2019.
Cary Hendricks, the Global Operations Director of ID Cyber Solutions, is former military and worked for years in cyber security with various agencies that used advanced tools to snoop on your data in search of criminals.
As part of Cary’s experience, he spent time working with sophisticated tools such as ‘eclipsed wing’, ‘dark pulsar’ and ‘eternal blue’ they belong to the National Security Agency of the USA. However, these tools were stolen about 3 years ago - they were used for monitoring and attacking remote desktop protocol sessions identifying vulnerable organizations to exploit. This leaves institutions of all sizes open to various attacks following the release of these tools, this is where incident response becomes an essential part of the organization.
Cary describes incident response as similar to a fire drill in your organization. The alarm goes off, you know where the document is, you know where the vest is, you know where the assembly points are, you know you must check everybody is out of the building. This process relates to incident response, you have to know who to call, know where your data is, know the people who are going to be involved, know what you’re going to say and how to learn from this.
What Is Incident Response?
Incident Response is a coordinated system for responding to a system breach. Incident Response is identified through a series of steps forming the process to be considered:
- Capabilities and processes (Do we have a plan to tackle this? What is our plan?)
- Readiness (How prepared is your organization with dealing like something like this?) Have you had any training or a plan for this event?)
- Team (Do we have a team? Internal or external? Do they know how to deal with something like this?)
- Cost/budget (How much money would we need? Is this readily available - immediate release money? The cost goes up quite significantly within the first 2,3 or 4 days to even £10-20k in dealing with it the first week.)
- Current security posture (What have you done to prevent any of these types of incidents? Have you enabled multi-factor authentication? Have you installed anti-virus? Have you been paying attention to the logs? How often do you look at those logs? Do you know where your data is? Do you know how your data is secured on the web/internal organization? Who has access to that? What kind of security policies do you have?)
- Strategy (now that we have people, a budget, a team, capabilities and processes etc but who is going to talk to the media, our customers?)
- Cyber insurance (Do you have insurance against an event like this? Will they pay up? How quickly will they pay up?)
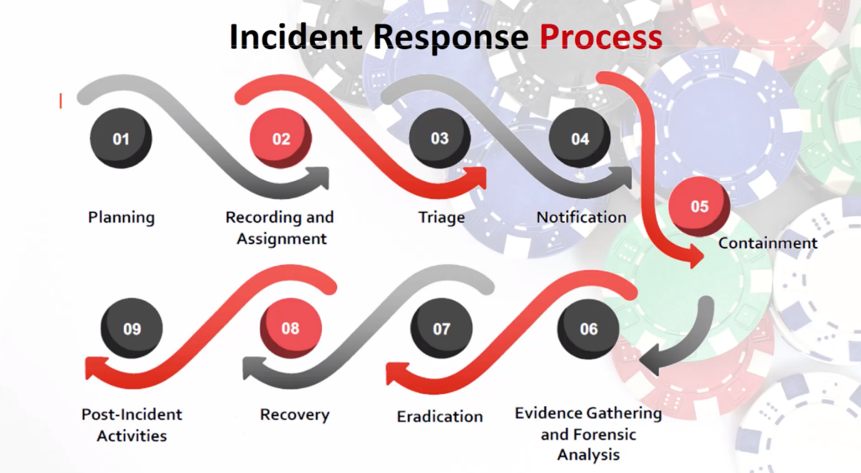
What is an Incident Response Process?
To mitigate the situation, the below steps are employed by a technically equipped team to promptly resolve the situation. The Incident Responders play an important role in the immediate manipulation of the incident if handled incorrectly the situation could escalate. The incident responder also engages in the aftermath effects of the incident, gathering information as to how the incident occurred and future prevention strategies.
What are the Most Common Types of Incidents?
- Malware incidents: Malware detections targeting businesses increased by 270% over the last few years with much more serious types of events - losing and destroying all of the organization's data and backups.
- Web app security incidents: Almost 90% of websites are vulnerable to some kind of attack. Better security is needed.
- Network security incidents: 21% of devices are exposed to network threats in the 1st month, rising to 43.7% after 4 months.
- Cloud security incidents: 681 million cyber attacks were launched against cloud customers in 2018 - very popular.
- Email security incidents: 9 out of 10 infection attempts throughout the year were spam email.
- Insider threats: 29% of breaches occur due to the malicious intent of insiders.
What are the Hacking Processes?
To really understand the reasons behind the process we must think in the way an attacker would. How would they get the information on the target to begin the attack? What chances do they have of being successful? How will they carry out the attack? When will it take place? What data are they looking for? Will they be looking to revisit the site in future?
Similar to incident response ethical hacking follows a strict process;
- Reconnaissance - finding information about the target (Who are the customers? Who works at the organisation? Email addresses etc) – 90% of a hack is spent in the reconnaissance phase.
- Enumeration - list all the information gathered about the target (How hard or easy is it going to be to attack you?)
- Hacking - using the information found in step 1 to formulate an attack. This can consist of running exploits against vulnerabilities identified within the system in the reconnaissance phase to gain access to the system.
- Access - access system and download data
- Hide - hide and harvest information (especially for long term)
Once we know the process, we can look at these areas where we can start to try and fix it.
What are the recommendations?
- Firewalls - the installation and proper configuration of firewalls to block access/protocols
- Secure configuration – ensuring strong configurations are in place on the system securing the services and devices
- Access control - Managing user access by enforcing strong usernames and password
- Patch management - ensuring the latest updates are applied and unused software is disabled or removed
- Malware protection – utilising antivirus ensuring it is fully updated and applying scanning techniques
All of these are part of a government scheme called Cyber Essentials so you can download the questionnaire to assess your organisation’s security plan.
How can you effectively protect businesses from Cyber Threats?
The steps follow the below categories:
- Cybersecurity training is essential and having a team that knows when and how to kick in is vital. Therefore, training needs to be invested in for staff to ensure for the smooth, safe running of an organisation.
- Know about the concepts of the threats. Understanding the threats your organisation faces is fundamental to the process of securing your business from these threats.
- Be able to collect evidence in assisting Law Enforcement - vital to report to police (phone 101 Police Scotland to report the cyber incident) - taking notes of everything.
- It is about everyone in the organisation participating in security - physical and cyber.
Defence in Layers

Preparing your teams
This latest iteration of EC-Council’s Certified Incident Handler (E|CIH) programme has been designed and developed in collaboration with cybersecurity and incident handling and response practitioners across the globe.
It is a comprehensive specialist-level program that imparts knowledge and skills that organisations need to effectively handle post-breach consequences by reducing the impact of the incident, from both a financial and reputational perspective. The Certified Incident Handler training course will significantly benefit Mid-Level to high-level managers and information security professionals who want to enrich their skills and knowledge in the field of incident handling and response.

Don’t wait until it’s too late for your organization!
Click HERE to book your course on Incident Handling with ID Cyber Solutions.

